What is a reverse proxy? Secure guide for VPN users
While virtual private networks (VPNs) like ExpressVPN protect your online traffic on the user side, reverse proxies protect websites and servers on the hosting side. Understanding how they differ and work together can help VPN users see the bigger picture of online security.
In this guide, we’ll explain what a reverse proxy is, how it works, and why it plays such a vital role in securing the web. You’ll also learn how reverse proxies improve performance, balance traffic, and protect against cyberattacks, giving you a clearer view of how online protection extends beyond your VPN.
What is a reverse proxy?
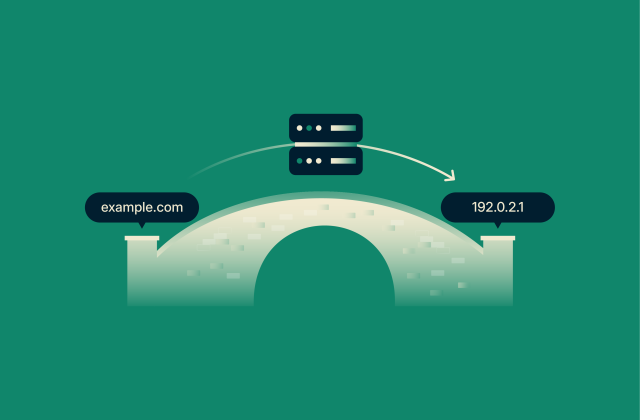
A reverse proxy is a server that sits between a website’s main server and its users, managing incoming requests before they reach the backend. Instead of connecting directly to the website’s server, your browser communicates with the reverse proxy, which forwards the request to the actual server and then returns the response.
Reverse proxies are a key part of how the modern web works. They help websites stay fast, secure, and reliable by managing high volumes of traffic, balancing server loads, and protecting against common cyber threats. Most large platforms and cloud services use reverse proxies as a standard layer of infrastructure, and even smaller websites often rely on them to enable HTTPS, boost performance, and add an extra layer of protection.
How a reverse proxy works
A reverse proxy acts as a smart middle layer between users and the servers that host a website or app. Here’s a simple breakdown of what happens when you visit a site that uses one:
- You send a request: You type a website address into your browser or click a link. That action sends a request to load the page.
- The request travels across the internet: Your data moves through the web toward the site’s hosting infrastructure.
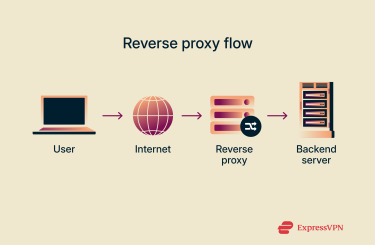
- The reverse proxy receives the request first: Instead of reaching the website’s actual server, your request stops at the reverse proxy. It decides how to handle the traffic and which server should process it.
- The proxy connects to a backend server: The proxy forwards your request to one of the website’s internal servers, usually the one that’s available or closest to you.
- The response is sent back through the proxy: The backend server returns the requested data (like a web page or video) to the proxy, which then delivers it to your browser.
Throughout this process, you never connect directly to the website’s real server. The reverse proxy keeps its IP address hidden and can filter or inspect traffic to block malicious requests before they reach the destination server.
Reverse proxy vs. forward proxy: Key differences
Both forward and reverse proxies act as intermediaries, but they sit on opposite sides of the network and serve very different purposes.
A forward proxy (often just called a “proxy server”) sits in front of users and handles their outgoing requests to the internet. It hides the user’s real IP address from websites and can block or filter specific websites, but its overall security and privacy vary greatly depending on specific implementations.
Forward proxies are commonly used in schools, offices, or by individuals who want more privacy, similar to how a VPN masks your online identity by routing traffic through its own secure servers.
A reverse proxy, on the other hand, sits in front of a web server and manages incoming traffic from users. It hides the server’s real IP addresses, balances load across multiple systems, and filters potentially harmful requests before they reach the site’s infrastructure.
| Forward proxy | Reverse proxy | |
| Position | In front of clients (users) | In front of servers (websites) |
| Main goal | Protect users and control outgoing requests | Protect servers and manage incoming requests |
| Hides | User’s IP address | Server’s IP address |
| Common uses | Privacy, content filtering | Load balancing, caching, distributed denial-of-service (DDoS) protection |
| Comparable to | VPN for users | Content delivery network (CDN) or load balancer for websites |
In short, a reverse proxy protects and optimizes the server side of the connection, while a forward proxy (or VPN) protects the user side.
Note: VPNs also sometimes use proxies internally for routing connections more efficiently. For example, ExpressVPN’s Lightway protocol supports HTTPS proxying.
Benefits of using a reverse proxy
A reverse proxy gives websites and applications a smart, protective layer. It improves how sites handle traffic, manage servers, and safeguard data.
1. Load balancing and traffic distribution
One of the standout advantages of using a reverse proxy is load balancing. When lots of users request content at the same time, a reverse proxy distributes those requests across multiple backend servers rather than letting one server become overwhelmed. And if one server fails or slows, the reverse proxy can send new requests to other available servers so the website keeps working.
Common load balancing strategies
Reverse proxies can distribute traffic using either dynamic or static load balancing methods.
Dynamic load strategies are flexible and scalable, automatically adapting to changes like new servers being added or temporary overloads:
- Least connection method: Sends new requests to the server handling the fewest active connections. Simple and efficient, though it doesn’t factor in how demanding each request might be.
- Weighted least connection: Takes capacity into account by assigning more traffic to servers with greater processing power.
- Weighted response time: Uses both response time and connection data to direct requests to the fastest, most available server.
- Resource-based method: Monitors CPU and memory usage across all servers and routes traffic to the one with the most available resources.
Static load balancing methods distribute requests according to fixed rules rather than real-time server performance:
- Round robin: The proxy cycles through servers in a fixed order. Each server takes turns handling requests.
- Weighted round robin: Similar to round robin, but gives stronger servers a higher “weight”, meaning they receive more requests than weaker ones.
- IP hash: Assigns users to servers based on their IP address, helping ensure returning users connect to the same server for a consistent experience.
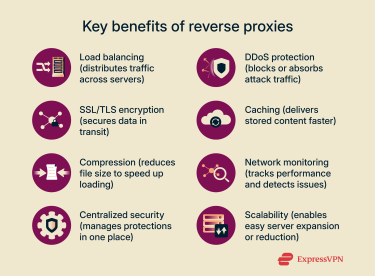
2. Security advantages
Reverse proxies also play a key role in strengthening a website’s security. They hide sensitive server details, filter incoming requests, and act as a first line of defense against cyberattacks. Because all traffic passes through them, they can inspect, encrypt, and control data before it ever reaches the core infrastructure.
SSL/TLS termination and encryption handling
A reverse proxy can manage encryption and decryption for all traffic that passes through it.
Instead of forcing each backend server to handle Secure Sockets Layer / Transport Layer Security (SSL/TLS) encryption separately, the proxy decrypts incoming requests and encrypts outgoing responses. This process (called SSL/TLS termination) reduces the workload on main servers, cuts operating costs, and ensures that every connection uses strong, up-to-date encryption.
By enforcing consistent SSL/TLS policies across all servers, reverse proxies help organizations meet data-protection standards and maintain regulatory compliance.
Protection against DDoS attacks
Because a reverse proxy sits between users and the origin server, it hides the real IP address of the protected server. This makes it harder for attackers to target the backend directly.
If a distributed denial-of-service (DDoS) attack floods the proxy with malicious requests, it can filter, block, or distribute that traffic across multiple servers. This prevents a single server from being overwhelmed and keeps legitimate users online even under attack.
Network health monitoring
Reverse proxies log all incoming and outgoing connections. By analyzing this data, administrators can detect unusual patterns (like traffic spikes or suspicious requests) before they escalate into security incidents. Over time, these logs help refine incident response policies and improve overall resilience.
Streamlined security policy management
Because all traffic passes through a single point, a reverse proxy simplifies how organizations manage security policies. Instead of configuring SSL certificates or firewall rules on every individual server, admins can enforce them directly at the proxy level. This centralized approach reduces errors, speeds up updates, and scales easily as new servers are added.
Reverse proxies make it easier to apply and maintain organization-wide protection rules in line with modern network security standards.
Rate limiting
Reverse proxies can also enforce rate limits, controlling how many requests a user or IP address can make within a set time. If a client exceeds the limit, the proxy simply drops extra requests before they reach the backend servers.
This keeps performance stable and helps mitigate both intentional DDoS floods and unintentional traffic surges from legitimate users. By managing rate limits intelligently, reverse proxies protect system resources and ensure fair access for everyone.
3. Performance improvements
Beyond balancing traffic and enhancing security, reverse proxies also make websites faster and more efficient. They optimize how data moves across the network, reduce the workload on backend servers, and simplify scaling as traffic grows.
Caching mechanisms
A reverse proxy can store copies of frequently requested content in its cache, allowing it to serve users quickly without contacting the main server each time.
When a user requests data that’s already stored in cache (like an image, a video, or a page), the proxy delivers it instantly. This reduces latency, saves server resources, and speeds up response times for everyone.
Caching becomes even more powerful in global networks. If a reverse proxy in one region retrieves and stores content, other proxies around the world can serve it from that cache, shortening delivery paths and improving performance for international users.
Compression and content optimization
Reverse proxies can also compress data before sending it to users. By using technologies like gzip or Brotli, they reduce the size of files, lowering bandwidth usage and improving load times, especially on slower connections.
Offloading compression tasks to the proxy means backend servers spend less time processing data and more time running core applications.
Easier network scalability
Reverse proxies make it easier to scale as user demand changes. When traffic spikes, administrators can add new backend servers without disrupting the existing setup. Because all traffic passes through the proxy, new servers are automatically recognized and added to the rotation.
This centralized configuration eliminates the need to adjust firewall or SSL settings on each server; admins only update the proxy, and the changes apply network-wide. Combined with dynamic load balancing, this ensures smooth performance even as the infrastructure grows.
Limitations of using a reverse proxy
Reverse proxies bring significant security, privacy, and performance advantages. However, like any network technology, they also come with potential drawbacks, especially when misconfigured. Understanding these risks helps administrators apply stronger protections and fail-safes during setup.
Cached and stored data
Reverse proxies cache website content to speed up response times and store connection metadata such as client IP addresses and session details.
While this improves performance, it also makes the proxy a valuable target for attackers seeking access to cached files or logs containing sensitive data. Proper cache encryption, access control, and data retention policies are essential to reduce exposure.
Single point of failure
Although reverse proxies protect networks by rerouting traffic from failed backend servers, the proxy itself can become a single point of failure if it goes down.
If the reverse proxy fails, all connected services may become unavailable. To prevent this, organizations often deploy failover configurations: secondary reverse proxies that automatically take over if the primary one stops responding.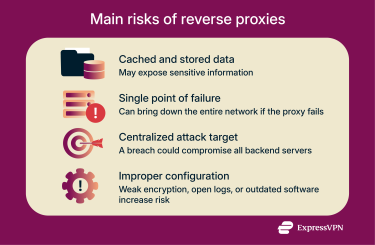
Centralized point of attack
Because a reverse proxy sits between users and multiple backend servers, it becomes a high-value attack target. A successful breach could expose or compromise all systems connected behind it.
However, this risk mainly applies to single-proxy deployments, where all incoming traffic flows through one entry point. Many organizations mitigate it by using a distributed or hybrid setup, where traffic is balanced across multiple reverse proxies, each routing requests to its own group of backend servers.
Improper configurations
Misconfiguration is one of the biggest security risks for reverse proxies. Poor setup can expose backend servers or sensitive data directly to the internet. Common configuration issues include:
- SSL/TLS implementation: Outdated or misconfigured encryption leaves data open to interception or decryption attacks.
- Unsecured logs: Logs can reveal server IP addresses, performance data, and vulnerabilities if not properly protected.
- Outdated software: Running old proxy software with known vulnerabilities can give attackers an easy entry point into the network.
Common use cases for reverse proxies
Reverse proxies are used across many industries to improve performance, security, and scalability. Here are some of the most common scenarios:
Content delivery networks (CDN)
CDNs rely on reverse proxies to speed up and protect content delivery across the globe. By routing user requests through strategically placed servers, they reduce latency and keep websites responsive, even under heavy demand.
Reverse proxies also handle essential CDN security functions: filtering harmful traffic, masking the origin server’s IP address, and distributing requests across available infrastructure to maintain uptime. In essence, they allow CDNs to deliver content that’s not only faster but also more secure and reliable worldwide.
API gateway scenarios
API gateways act as a single entry point for apps that connect to multiple backend services. Reverse proxies enhance their efficiency by routing and combining requests.
Instead of sending several separate requests to different APIs, a reverse proxy aggregates the data and returns one optimized response. This reduces latency, network overhead, and the number of client-to-server round trips.
E-commerce and high-traffic websites
Online stores and large web platforms often use reverse proxies to handle sudden traffic spikes. During major sales events, caching and load balancing keep pages responsive and prevent outages by spreading requests evenly across servers.
Corporate and enterprise security
Reverse proxies also strengthen enterprise security. They inspect and filter incoming traffic, enforce SSL/TLS encryption, and apply company-wide security policies before requests reach internal servers.
By hiding server IP addresses, reverse proxies reduce the attack surface and help isolate internal resources from the public internet.
Setting up a reverse proxy
Before you implement a reverse proxy, start by defining your key goals around performance, security, and traffic management. These will guide your vendor selection, necessary features, and system compatibility requirements.
1. Choosing between Nginx, Apache, and other options
Nginx and Apache remain two of the most widely used open-source options for web servers and reverse proxies. According to W3Techs, Nginx is powering about 33% of sites and Apache about 25% as of October 2025.
Note: You can see the source code for Nginx and Apache HTTP Server on GitHub.
Open-source tools give you flexibility and customization, but remember that they may lack dedicated vendor support compared to commercial alternatives.
If you prefer full vendor support and integrated services, commercial solutions (for example, from established CDN or network security vendors) offer enterprise-specific customizations, though with less flexibility for deep configuration.
2. Advanced features and optimizations
Once you’re up and running, you’ll want to look beyond basic request routing. Consider features like dynamic load balancing algorithms, failover configurations, SSL/TLS termination, and protocol optimizations. What you need depends on your traffic profile and performance goals, so involve network engineers and infrastructure teams early.
3. Security implementations and considerations
A well-configured reverse proxy can significantly strengthen your network security, but it requires ongoing maintenance and oversight. Use these best practices to minimize risk and ensure long-term stability:
- Establish clear management policies: Define who manages the reverse proxy, how updates are deployed, and how credentials or certificates are handled. This ensures continuity during staff or vendor transitions.
- Keep software up to date: Regularly update proxy software, modules, and dependencies to patch known vulnerabilities before attackers exploit them.
- Schedule regular security audits: Conduct periodic reviews to test configuration integrity, certificate validity, and server response behavior.
- Enforce least privilege: Limit the access and permissions granted to reverse proxies so they only handle the specific resources required for their function.
- Implement continuous monitoring: Track proxy health, resource usage, and unusual traffic patterns. Enable alerting systems for anomalies that could indicate intrusion attempts.
- Enforce end-to-end encryption: Require SSL/TLS across all connections (from clients to the proxy and from the proxy to backend servers) to prevent man-in-the-middle (MITM) interception.
FAQ: Common questions about reverse proxy servers
What is the difference between a proxy and a reverse proxy?
Proxies and reverse proxies differ primarily in placement and functionality. A proxy (often called a forward proxy) sits between users and the internet, forwarding client requests to external servers. It hides the client’s identity and is typically used for privacy, content filtering, or access control.
A reverse proxy, on the other hand, sits in front of web servers. It receives client requests, forwards them to the appropriate backend server, and returns the response as if it came directly from the proxy. This setup hides and protects servers, improves performance through caching and load balancing, and adds a security layer.
Is a reverse proxy safe to use?
Reverse proxies from reputable providers are safe to use. They screen network traffic for malicious requests before they reach backend servers. Reverse proxies also mitigate distributed denial-of-service (DDoS) attacks by distributing malicious and legitimate traffic across servers, preventing any single server from being overwhelmed.
What are real-world examples of reverse proxies?
Common reverse proxy applications include content delivery networks (CDNs), high-traffic websites, and e-commerce platforms. Content caching on reverse proxies enables faster website response times by serving stored data without repeated server queries. CDNs also use load balancing on proxy servers to distribute traffic across multiple destination servers, managing high volumes and traffic spikes effectively.
How does a reverse proxy improve security?
A reverse proxy improves security by hiding the IP addresses of origin servers, making them harder to target directly in attacks like distributed denial-of-service (DDoS). It can also filter or block malicious traffic and distribute incoming requests across multiple servers, helping maintain uptime and prevent overload during large-scale attacks.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN