Domain hijacking vs. DNS poisoning: Key differences and how to stay protected

Domain-based attacks, which target the control or resolution of internet domains, are one of the major cyber threats of today. Two common and high-impact forms of domain-based attacks are domain hijacking and Domain Name System (DNS) poisoning.
In this article, we examine how domain hijacking and DNS poisoning work, explore the key differences between them, and provide actionable guidance to help protect your domains and networks from these growing threats.
What are domain-based cyberattacks?
Domain hijacking and DNS poisoning are both forms of domain-based cyberattack, which is a general term for malicious activities that target internet domains or the systems that control them. These attacks aim to compromise the security, integrity, or availability of a domain, often to steal information, redirect traffic, or disrupt online services.
The consequences of domain-based attacks can be significant. They may enable or facilitate phishing attacks and man-in-the-middle attacks (MITM), cause website downtime, redirect traffic without authorization, and more. Understanding these attacks can help domain owners and network administrators identify potential risks and implement measures to protect their domains and users.
What is domain hijacking?
When you register a domain name, you do it through a domain registrar, a company that manages your ownership and control over that domain. This control includes things such as deciding which server or IP address your domain resolves to, who can update DNS records or change domain settings, and how the domain’s DNS records are configured.
Domain hijacking, also known as a domain takeover, occurs when a threat actor takes control without authorization. In effect, the attacker becomes the new owner of your domain.
How domain hijacking works
Common techniques to accomplish domain hijacking include:
- Social engineering: Social engineering is when a threat actor manipulates a victim into revealing sensitive information or performing actions that compromise security. For example, an attacker might impersonate a domain registrar in a phishing email and trick the domain owner into giving away their login credentials. Once the attacker has these credentials, they can access the registrar account and take control of the domain.
- Exploiting expired domains: Domains are leased for fixed periods and must be renewed periodically. If the owner of a domain fails to renew it on time, an attacker can register it and become its new owner.
- Registrar system vulnerabilities: If a registrar’s platform or processes aren’t secure, attackers can exploit flaws to gain access to domain accounts or modify domain settings.
- Compromised API keys or authentication tokens: Some registrars allow automated access via API keys or tokens. If these are acquired by a threat actor, they could be used to make unauthorized changes.
Signs and consequences of a domain hijacking attack
Domain hijacking can have serious ramifications. When an attacker gains control of your domain, they can perform DNS redirection, sending visitors to malicious sites or other unintended destinations. They can also take over email accounts, disrupt services, damage your brand’s reputation, cause financial losses through downtime or fraud, and even trigger legal or regulatory complications if sensitive data is exposed.
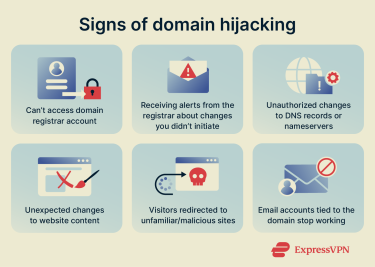
Here are some signs that your domain may have been hijacked:
- Inability to access your domain registrar account.
- Receiving alerts from your registrar about password changes, account transfers, contact updates, or unauthorized domain transfers.
- Unexpected changes to DNS records or nameservers.
- Unexpected changes to website content.
- Reports that visitors to your domain are being redirected to unfamiliar or malicious sites.
- Email accounts tied to the domain have stopped working, which can occur if an attacker changes your domain’s mail settings or MX records.
How to prevent domain hijacking
Here are some simple ways to protect yourself from domain hijacking:
- Choose a reputable registrar: Select a registrar with strong security practices, responsive support, and features like two-factor authentication (2FA) and domain locking.
- Use strong, unique passwords: Ensure your registrar account password is long, complex, and not reused across other accounts.
- Enable 2FA: 2FA adds an extra verification step that helps prevent unauthorized access, even if your credentials are compromised.
- Keep contact information up to date: Make sure your registrar has your current email addresses and phone numbers so you receive important notifications about domain changes or renewals.
- Monitor domain activity: Regularly check DNS records, nameservers, and registrar account activity so you can catch any suspicious activities quickly.
- Enable domain or registrar locks: Many registrars offer a lock feature that prevents your domain from being transferred or altered without your explicit approval. For additional protection, some registries also provide a “registry lock” that adds a higher level of change control.
- Be cautious with emails and links: Avoid clicking links in suspicious emails claiming to be from your registrar; if you’re not sure whether the email is legitimate, contact your registrar directly via the official support channels rather than responding to the email. Also, remember to always verify a URL before entering your login credentials.
- Renew domains promptly: Keep track of expiration dates and renew domains before they lapse to prevent attackers from registering them once they expire.
What to do if your domain is hijacked
If your domain has been hijacked, acting quickly is essential. Domain recovery is often possible if you can prove legitimate ownership and follow the proper channels. The following steps are recommended:
- Secure your accounts and devices: Scan your devices for malware, as attackers often gain access through infected systems or stolen login credentials. Change passwords for your registrar and email accounts, ideally from a different, trusted device. Finally, enable multi-factor authentication on your registrar and email accounts to prevent further unauthorized logins.
- Contact your registrar: Ask them to freeze any further transfers or modifications while you work through recovery. The registrar can also review logs and transfer records to confirm what happened and guide you through restoring control.
- Gather documentation to prove ownership: Prepare evidence such as registration records, renewal notices, billing receipts, or past correspondence showing that you’re the legitimate owner. Providing clear documentation will help your registrar verify your identity and expedite the recovery process.
- Contact ICANN if your registrar is unresponsive: If your registrar won’t assist you or fails to act, submit a complaint to the Internet Corporation for Assigned Names and Numbers (ICANN) using its official transfer complaint form. ICANN can request that the registrar investigate the case and take corrective action.
- Escalate through official dispute channels if needed: If the hijacker has transferred the domain to another registrar, your original registrar can file a formal complaint under ICANN’s Transfer Dispute Resolution Policy. In cases involving trademarked domains, you may also submit a complaint to a dispute resolution provider, such as the World Intellectual Property Organization (WIPO).
Subdomain hijacking
Subdomain hijacking is a cyber threat related to domain hijacking, but it works differently. A subdomain is part of your main domain (like blog.example.com), and it can be set up in several ways, including using a canonical name (CNAME) record, which tells DNS to point the subdomain to another domain or service.
The most common way subdomain hijacking happens today is through a dangling CNAME. This occurs when a CNAME points to a cloud service or software-as-a-service (SaaS) resource (for example, a website hosting service or a storage bucket) that was associated with a specific account or project and is later deleted. When the resource is removed, the subdomain points to an address that no longer exists. An attacker can then create a new account or project with the same name and take control of that address, effectively “claiming” the subdomain without ever touching the main domain.
In other words, the subdomain can be hijacked even if the main website is secure. This is particularly risky for large organizations, which often have many subdomains and may not track all of them, especially ones that are no longer in use.
To protect against subdomain hijacking, regularly review your DNS settings and remove any outdated CNAME records that point to services no longer active. If a subdomain is compromised, update or delete the DNS record immediately. For CNAMEs pointing to third-party services, contact the provider to reclaim the resource or disable the hijacked service.
What is DNS poisoning (cache poisoning)?
The DNS helps direct users to the correct website when they type a domain name into the address bar of their browser. DNS poisoning, also called DNS cache poisoning, occurs when an attacker inserts false information into this system, so that it directs users to the wrong website.
DNS poisoning shouldn't be confused with DNS hijacking, which is another method attackers use to redirect users without altering the DNS system itself.
How DNS poisoning works
In order to understand how DNS poisoning works, we need a basic understanding of how DNS works. When you want to visit a website, your device needs to know the domain’s IP address. To acquire this information, it asks a DNS resolver. The DNS resolver looks up the answer and then stores (or caches) the answer temporarily so it doesn’t have to repeat the lookup if another device asks for the same domain soon after.
Caching makes the web faster, but it also creates a single point that an attacker can target: if the cache contains a false address, every client that relies on that resolver can be redirected to the wrong place.
There are two main methods threat actors use to poison a DNS cache (i.e., insert a false IP address into the cache), and both are forms of DNS manipulation. The first is sending forged replies, commonly known as DNS spoofing. When a DNS resolver doesn’t know an IP address, it asks another server for the answer and waits. While it’s waiting, an attacker can send it a fake reply. All resolvers perform some validation of incoming replies, but those with weak or predictable checks may store false information in their cache, allowing the attack to succeed.
The second method is compromising the resolver. An attacker who gains unauthorized access to the DNS server can directly alter its cached records.
Signs and consequences of DNS poisoning
A successful DNS poisoning attack can have serious effects for both users and organizations. If users are redirected to malicious sites, they may have sensitive personal information, such as passwords or payment details, stolen. Malicious sites may also deliver malware, including spyware, ransomware, or keyloggers.
For organizations, DNS poisoning can lead to reputational damage, loss of customer trust, reduced traffic and revenue, lower search engine rankings, and more.
Common signs that point to potential DNS poisoning include:
- Users are redirected to unfamiliar or suspicious websites
- Browser warnings about certificates or security issues (e.g., the site’s Transport Layer Security (TLS) certificate doesn’t match the expected domain)
- Broken or incomplete website functionality; pages may load slowly, images might be missing, or forms may not work properly because resources are being loaded from the wrong server
- Unexpected changes in DNS records
How to prevent DNS poisoning
Here are some practical steps network administrators can take to prevent DNS poisoning:
- Enable DNSSEC: Domain Name System Security Extensions (DNSSEC) adds digital signatures to DNS records, allowing resolvers to verify that the responses they receive come from the correct source and haven’t been tampered with. For DNSSEC to provide protection, both the domain must be signed and the DNS resolver used by clients must perform DNSSEC validation.
- Use unpredictable DNS queries: For administrators running their own DNS servers, random source ports, query IDs, and mixed-case domain names make it much harder for attackers to craft fake responses that will be accepted by your server.
- Keep DNS software updated: Regularly patch your DNS servers to close security gaps that attackers could exploit.
- Monitor and log DNS activity: Check DNS records and server logs regularly. Monitoring tools or intrusion detection systems can help spot unusual activity early.
- Educate staff and stay informed: Train your team on DNS security and phishing risks, and follow updates from security sources to stay aware of new threats.
What to do if your DNS is poisoned
If you suspect your DNS has been compromised due to poisoning, it's crucial to act swiftly to mitigate potential damage and restore security. The following steps are recommended:
- Restore DNS records: Immediately revert any altered DNS records to their original configurations.
- Isolate affected servers: Disconnect or isolate any DNS servers suspected to be compromised. This action prevents the spread of malicious entries and protects other parts of your network.
- Clear DNS caches: Flush the DNS cache on affected servers to remove poisoned entries.
- Apply security patches: Identify and update any systems or software within your network that may have been exploited during the attack. Applying the latest security patches helps close vulnerabilities and prevent further exploitation.
- Monitor for ongoing issues: Implement real-time monitoring and intrusion detection systems to detect and prevent future DNS cache poisoning attempts. Continuously monitor DNS traffic and log any suspicious activity.
Domain hijacking vs. DNS poisoning: Key similarities and differences
Domain hijacking and DNS poisoning are both domain-based attacks; they exploit DNS-related vulnerabilities to interfere with the normal flow of internet traffic.
However, they differ in how the attacks are carried out, who suffers the effects, the attackers’ motives, how serious the fallout can be, and how long the impact typically lasts. The table below summarizes the key differences.
| Domain hijacking | DNS poisoning | |
| Attacker’s methods | Gaining unauthorized control of a domain via registrar compromise or credential theft | Inserting false DNS information into a resolver’s cache so it returns the wrong address |
| Who’s affected | The domain owner, users visiting the domain | Users who try to visit the affected domain while the DNS server has the fake address in its cache (and the domain owner indirectly via lost traffic, etc.) |
| Attacker’s goals | Full domain takeover for profit or sabotage | Redirect visitors to attacker-controlled sites for malware delivery or credential harvesting |
| Potential consequences | Loss of control over the domain, redirected traffic, service disruptions, intercepted email/communications, site defacement, legal fallout, loss of revenue, and more | Malware infection, credential or data theft, potential reputational damage |
| Persistence | Often long-lasting; remains until domain ownership is recovered | Typically transient; lasts until the poisoned cache entry expires or is cleared |
Cybersecurity tools that help protect your domain and network
There’s a range of cybersecurity tools that can help domain owners protect against both domain hijacking and DNS poisoning:
- Password managers: Tools like ExpressKeys generate, store, and autofill strong, unique passwords across all domain-related accounts, reducing the risk of compromise from weak or reused credentials.
- Endpoint security software: Antivirus software and other endpoint protection tools defend devices against malicious software that could steal login credentials or session data, which attackers might then use to compromise domain accounts or DNS settings.
- VPNs and secure networking tools: VPN services, like ExpressVPN, encrypt the administrator’s connection, protecting sensitive traffic from interception, credential theft, or MITM attacks that could be used to hijack domain accounts.
- Monitoring services: Tools like UptimeRobot help you track DNS changes, domain activity, and administrative actions to detect unusual events early.
- Backup and recovery services: Many DNS providers offer automated backup and restore features for DNS configurations and domain records. These features enable rapid restoration if records are changed accidentally or maliciously, supporting domain availability and control.
Best practices for end users
Even if you don’t manage a domain, you can still be affected by domain hijacking or DNS poisoning. If you visit a domain that’s been hijacked or use a DNS resolver that’s been poisoned, you could be tricked into revealing personal data, downloading malware, or otherwise compromising your security. Here are some tips to stay safe:
- Check the URL: In some cases, it’s possible to identify a fraudulent website by carefully examining the URL. Look for typos, extra words, or unusual domain extensions (e.g., “.com” instead of “.org”) that may indicate you’re not on the site you intended to visit. This is especially important when visiting sites where you plan to enter sensitive information, such as login credentials or payment details.
- Watch for broken or unusual website behavior: Other signs that you may not be on a legitimate website include pages that load slowly, have missing images, broken forms, or different content than what you normally expect.
- Use a trusted DNS resolver: Consider using DNS resolvers from reputable providers that include built-in security features like phishing protection and DNSSEC validation.

- Keep devices and software updated: DNS poisoning or domain hijacking can redirect you to malicious websites that attempt to exploit vulnerabilities in your browser, operating system, or other software to infect your device with malware. Installing updates and security patches regularly helps close these vulnerabilities and protect your devices.
- Use antivirus software: This provides an additional layer of protection if you accidentally visit a compromised site.
- Pay attention to browser security warnings: Browser warnings about invalid or mismatched certificates, HTTPS errors, or other security alerts can indicate DNS poisoning or a hijacked domain. Don’t ignore these warnings.
FAQ: Common questions about domain hijacking vs. DNS poisoning
What is the difference between spoofing and poisoning?
Domain Name System (DNS) poisoning is the result, and spoofing is one method attackers use to achieve it. In DNS spoofing, an attacker sends forged DNS responses to a resolver to trick it into accepting false information. When the resolver stores this incorrect information in its cache, cache poisoning occurs, redirecting users to malicious sites until the cache is cleared.
What is the difference between DNS sinkholes and DNS poisoning?
Domain Name System (DNS) sinkholes and DNS poisoning both manipulate DNS traffic, but they serve opposite purposes. A DNS sinkhole is a defensive strategy in which a DNS server detects requests to known malicious or unwanted domains and responds with safe or controlled information, preventing users from reaching harmful sites.
DNS poisoning is an attack method where malicious actors insert false information into a DNS resolver's cache. This leads to legitimate users being redirected to malicious sites, often without their knowledge. In short, DNS sinkholes protect users, while DNS poisoning exploits them.
Can I recover a hijacked domain from a hacker?
Yes, recovering a hijacked domain is possible if you act quickly and provide documentation proving you’re the rightful owner. Contact your registrar immediately and supply evidence such as registration records, billing receipts, or correspondence showing prior control of the domain. The success of recovery depends on your registrar’s policies and how promptly you respond.
How often should I change domain or registrar passwords?
Passwords should always be updated promptly if there’s evidence of compromise, such as a data breach or unusual account activity. If there are no such signs, it’s generally more important to focus on creating strong, unique passwords, storing and sharing them securely, and enabling multifactor authentication.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN